Setting up basic authentication on a specific page
Estimated Time: 5 minutes
Overview
In KurocoEdge, basic authentication can be easily set up in the Edge settings page.
However, the above settings will apply the basic authentication to the entire website.
In this tutorial, we will go through the steps to set up basic authentication on the /docs/ subdirectory of the website using KurocoEdge.
What You'll Learn
How to set up basic authentication on a specific page on your website using KurocoEdge.
Prerequisites
This tutorial assumes that you know the basic of HTTP basic authentication.
Rule setup
Creating a rule
Select a draft deployment and add a rule by clicking the Add button.
General tab
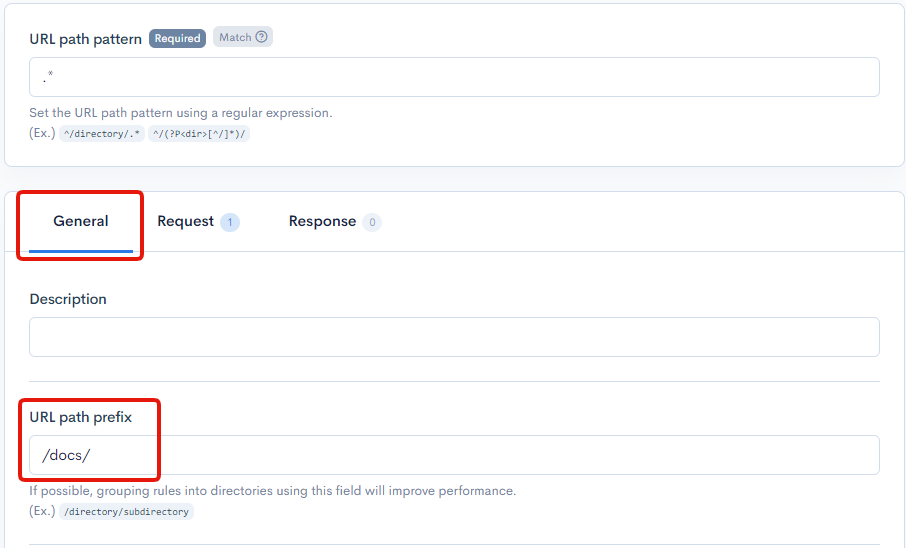
In the General tab, set the URL path prefix to /docs/ to apply this basic authentication rule to the /docs/ subdirectory.
Request - Execution
Next, go to the rule's Request tab, then expand the Execution section and add a Synthetic response field with the following settings.
| Field | Settings |
|---|---|
| Field settings | Synthetic response |
| HTTP Status | 401 Unauthorized |
| Body | <html><body>Unauthorized</body></html> |
| Headers | Name: Content-Type ; Value: text/html; Charset=UTF-8 Name: WWW-Authenticate ; Value: Basic realm="KurocoEdge" |
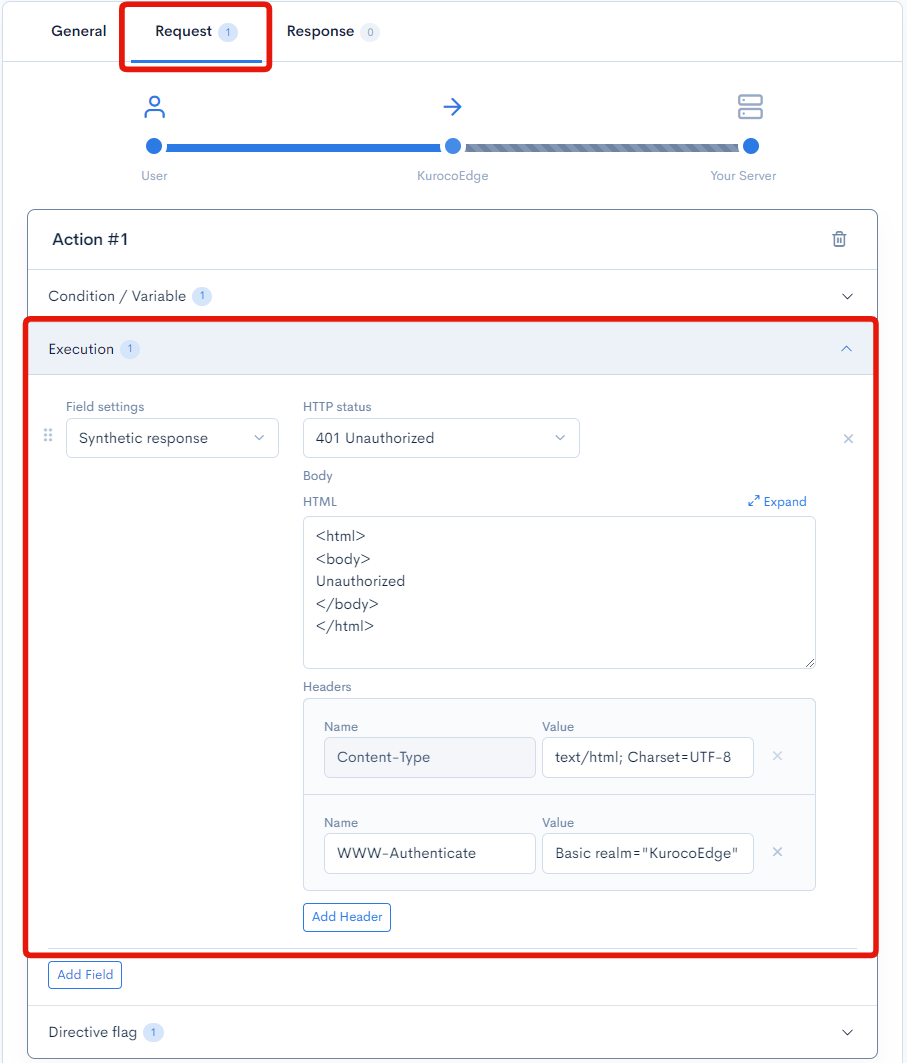
In the above configuration, KurocoEdge will return a 401 HTML response with the WWW-Authenticate header, which will prompt user for the login credentials.
Request - Condition / Variable
Next, we will need to add a condition to validate the credentials entered by the user.
In HTTP basic authentication, the credentials are encoded using Base64. In this example, we will use the login credentials test:test which will be encoded to dGVzdDp0ZXN0.
To encode or decode your own credentials, you can use https://www.base64encode.org/.
To set up the credential validation rule, under the Request tab, expand the Condition / Variable section and add a Header field with the following settings.
| Field | Settings |
|---|---|
| Field settings | Header |
| Header field | Authorization |
| Value pattern | Basic dGVzdDp0ZXN0 |
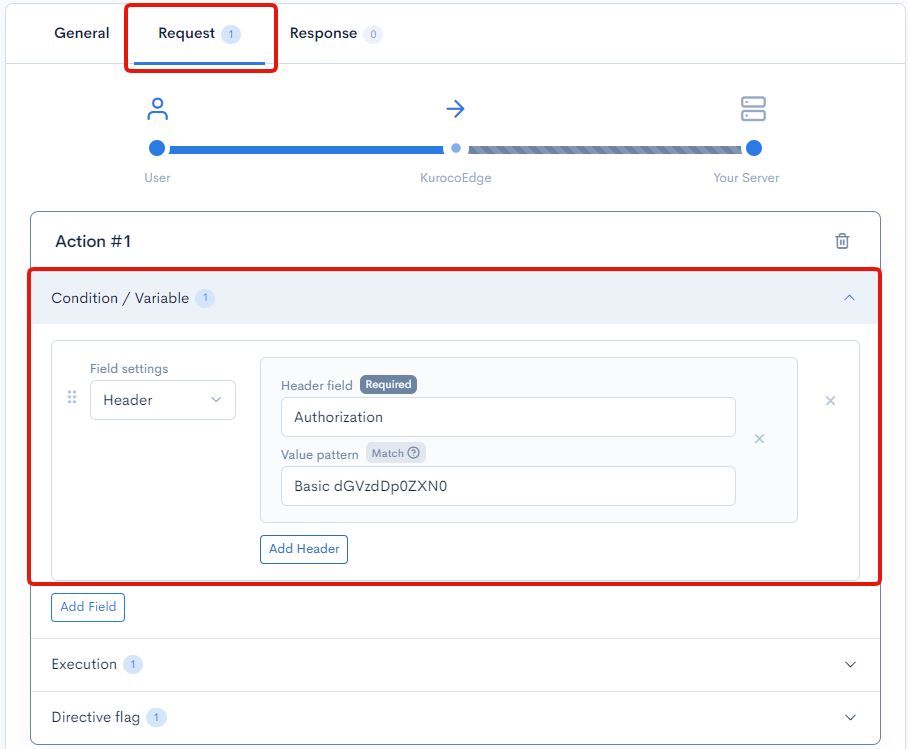
In the above configuration, we've added the condition to check Authorization header in the user's request to validate the credentials entered by user, Basic indicates that the authorization type is basic authentication, followed by dGVzdDp0ZXN0 which is the Base64 encoded credentials of test:test.
In KurocoEdge, negative lookaheads in regular expressions are not supported for performance reasons, which means conditions could not be set up with the "does not match" expression. This results in the condition configured above to return TRUE only when the credentials entered by the user are valid, which means that the Synthetic response in the Execution will only run whenever the user enters the correct credentials. This is opposite of what we want; therefore, we will need to add one last setting below.
Request - Directive flag
Finally, we will need to invert the condition's result so that the 401 HTML response is only sent when the credentials entered by the user do not match.
Expand the Directive flag section and enable the Invert conditions result.
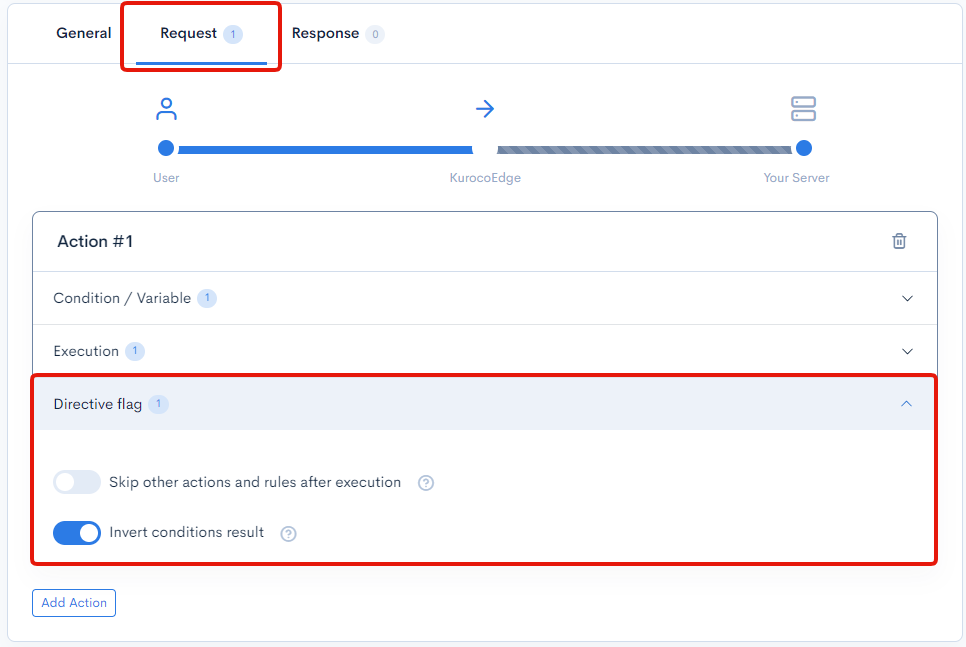
The configuration above will make it so that the Header that was added in the Condition / Variable tab to return TRUE when the credentials do not match and subsequently send the 401 HTML response, and if the credentials entered by the user is correct, then the Header condition will return FALSE and allow user to access the /docs/ subdirectory as the 401 HTML response will no longer be sent.
Validating the rule
Click the Update on the bottom left of the page to save your changes.
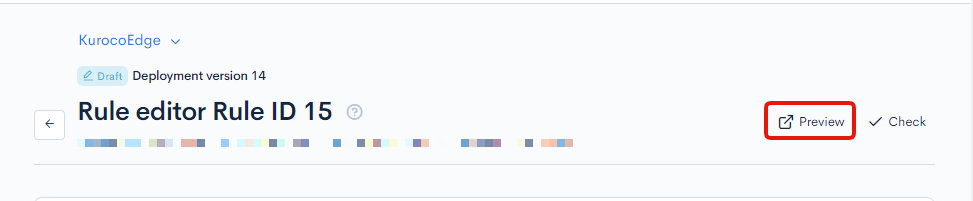
Finally, test the rule by clicking on the Preview button.
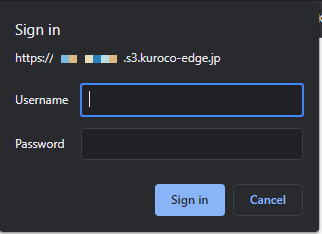
Verify the basic authentication login prompt appears when navigating to the /docs/ subdirectory.
Summary
By following this tutorial, you've learned how to set up basic authentication for specific pages on your website using KurocoEdge, with no source code changes required on your server.
Having multiple basic authentication checks for the same resource creates a situation where a user's single authorization header will always be invalidated by at least one of them - unless all of them share the same credentials. Therefore, you should avoid having to create resource-specific basic authentication rules if you have a global one (configured on Edge Settings admin panel or on the backend directly)
Support
If you have any other questions, please contact us or check out Our Discord Community.